Ethernet and Token Ring LAN technologies operate in different ways and both systems have their inherent advantages and disadvantages. The decision on which topology to use can be influenced by a number of factors. The most common factors to consider are cost, reliability, speed, size, administration, security and growth.
Ethernet is a frame-based computer networking technology for local area networks (LANs). It defines wiring and signaling for the physical layer, and frame formats and protocols for the media access control (MAC)/data link layer of the OSI model. Ethernet is mostly standardized as IEEE 802.3. It has become the most widespread LAN technology in use during the 1990s to the present day. Each network peer has a globally unique 48-bit key known as the MAC address factory-assigned to the network interface card (NIC), to ensure that all systems in an Ethernet LAN have distinct addresses. Due to the ubiquity of Ethernet, many manufacturers build the functionality of an Ethernet card directly into a motherboard.
Ethernet LAN

The advantages of Ethernet are cost, availability of materials, the fact that most PCs come with network cards that support Ethernet connectivity and speed. Data transfer rates can range from 10 Mbps to 10 Gbps. The main disadvantages are as network loads increase performance goes down and troubleshooting network issues can be difficult if you are using a bus topology.
The token ring architecture was developed by IBM in the mid 1980s and provides users with fast, reliable data transport. Token ring is based upon the IEEE 802.5 standard and the networks are wired in a star topology configuration but act as a logical ring.
The main advantages that token ring offers over Ethernet are a more efficient use of network resources between users, better network stability and network expansion can be achieved without a significant drop in performance. The ring topology allows for users to share traffic without necessarily overloading the network. The obvious disadvantages are cost and the complexity of implementing such a network.
Token Ring LAN
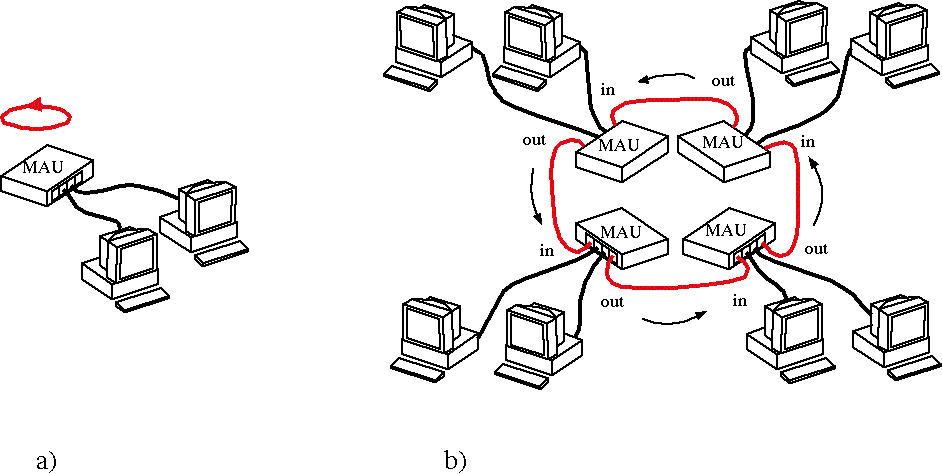
Ethernet uses CSMA/DC media access control and Token Ring uses token passing. This makes Ethernet better suited in a situation where there are a large number of computers sending fewer, larger data frames. Token Ring is better suited for small to medium size LANs sending many, smaller data frames.Ethernet has become the chosen network architecture for networks of any size. Its availability in most PCs, cost effectiveness, near universal adoption has made it the dominant architecture. Advances for token ring technology have been slow and can not keep pace with the advances in Ethernet. Furthermore, most major networking equipment manufactures have steered product development away from token ring to primarily focus on Ethernet. Token ring will soon reach near obsolescence along with other little used technologies such as ARCNET and FDDI.
One scenario where token ring may be used over Ethernet is in the case of a travel agency. Each travel agent would need to frequently access data over a network for reservation and booking information. In a token ring topology, each request would be sent to each user station so that all users have access to the data in the order that their machines are connected in the ring. The data would be transported over the network to each user instead of having that data travel to each individual user at the time that it's requested. By organizing how data is accessed, token ring offers a more efficient data access method. If one were to use an Ethernet network in this situation, the network would experience constant bottlenecks every time more than one user wanted to access the reservation database. Ethernet doesn't work well in environments where data is frequently accessed over the network by many users. Token ring allows for speedy yet efficient data access methods leading to fewer bottlenecks. Furthermore, the test procedures implemented with this topology would be helpful to troubleshoot and maintain the network.
An application where Ethernet would be advantageous over a token ring LAN would be a home network. Most modern PCs are equipped with NIC cards that are Ethernet ready, network cables and routers are relatively inexpensive and easy for the consumer to purchase. On the other hand, most NIC cards don't offer support for token ring and one would be hard pressed to find hubs that allow you to set up such a network. The cost and convenience factor alone would rule out token ring for a home network application. Since most users of a home network are not accessing data frequently, its major technological advantage becomes inconsequential. A home network allows users to share an internet connection and files from 2 or more machines. It will be rare for both machines to access the same data simultaneously or require that data to be sent throughout the network. Many Ethernet network cards can handle data transfer rates of 10-100 Mbps as the standard. If one were to implement a token ring LAN, they would be limited to either 4 or 16 Mbps. Since most home network users are concerned with cost, data transfer rates and ease of use, the logical choice would be to implement an Ethernet bus network.
In conclusion, the major advantages of Ethernet outweigh its disadvantages compared with token ring. Token ring still has a place in networks where data is frequently accessed over the network. For example, the reservation system used in a travel agency. In the case of most users, the simplicity, speed and availability of Ethernet makes the most sense for a network implementation.
Source: http://en.wikipedia.org/wiki/Token_ring
http://en.wikipedia.org/wiki/Ethernet2. Although security issues were not mentioned in this chapter, every network owner must consider them. Knowing that open networks all data to pass to every node, describe the posssible security concerns of open network achitectures. include the implicatiions of passing logon procedures, user IDs, and passwords openly on the network.
In the development of computer networks, the spread of malicious network activities poses great risks to the operational integrity of many organizations and imposes heavy economic burdens on life and health. Therefore, risk assessment is very important in network security management and analysis. Network security situation analysis not only can describe the current state but also project the next behaviour of the network. Alerts coming from Firewall and other security tools are currently growing at a rapid pace. Large organizations are having trouble keeping on top of the current state of their networks. The implicatiions of passing logon procedures, user IDs, and passwords openly on the network are great risk to protect critical information on the network. Appropriate access controls assist to protect information processed and stored in computer systems. The organisation's system security policy must clearly define the needs of each user or group to access systems, applications and data. The file-access rights should be configured according to business requirements and the "need to know" principle. Formal procedures should control how access is granted to information-system services or how such access is changed, so as to prevent unauthorised access to data or system resources. Access control can start by allowing access to everything, and then revoking access to whatever systems, applications or data repositories a user does not need. However, it is better to start by denying access to everything, and then explicitly granting access to just the specific resources a user needs. Secure logon procedures can control access to host-based information systems. Logon procedures should reveal minimal information about the system, to deter unauthorised use.
Source:http://support.novell.com/techcenter/articles/ana19960802.html
3. Remembering the discussion of deadlocks, if you were designing a networked system, how would you manage the treat of deadlocks in your network? Consider all of the following: prevention, detection, avoidance, and recovery.
In an apparatus having a network including successive stages of cross-point switches which collectively interconnect a plurality of nodes external to said network, wherein at least one message is carried between one of the nodes and one of the cross-point switches over a route through said network, a method for preventing routing deadlocks from occurring in the network which comprises the steps of: creating a graphical representation of the network; searching for the existence of cycles within the graphical representation; partitioning the graphical representation into at a first subgraph and a second subgraph if cycles exist in the graphical representation; searching for the existence of edges directed from the first subgraph to the second subgraph; and removing the edges directed from the first subgraph to the second subgraph. Preferably the step of partitioning the network into at a first subgraph and a second subgraph is performed such that the first subgraph and the second subgraph have an equal number of vertices, a number of directed edges from the first subgraph to the second subgraph is minimized so as to minimize the number of routes prohibited, and a set of partition constraints are satisfied. The method is recursively applied to the first subgraph and then the second subgraph, thereby removing all of the deadlock prone cycles in the network while minimizing the number of routes prohibited due to remove edges.
4. Assuming you had sufficient funds to upgrade only one component for a system with which you are familiar, explain which component you would choose to upgrade to improve overall performance, and why?
At present, both business and personal transactions take place through the computer more specifically through the Internet. Be it banking or job interview the need for an optimized computer with all the latest add-ons is imperative. Therefore the need for a user-friendly registry cleaner, easily assessable and trouble free operating system is the need of the hour. The system registry is where both the much needed as well as some unnecessary datas are stored for the smooth running of the system. Every time the system connects with the registry to open, install or run programs on a computer. Thus considering the registry as an important component in a computer a clean registry has to be maintained for hassle free performance. Windows registry cleaner help maintains the registry operations by scanning and cleaning up the problematic fragments which cause error messages or slows down the system performance. The registry cleaner also secures the important configuration and other password related files for future usage. The registry cleaner also setup startup registry cleaning function which might automatically cleanup the registry on every startup of the computer. The registry cleaner can also identify missing or corrupt hardware drivers, or orphaned software programs during its operation. It is a vivid report about the files cleaned and the error files with which you can either manually or automatically clean up the registry. Many free registry cleaner downloads are available and it is important to choose the right registry cleaner suited to your system requirements. For the sole purpose of maintaining a clean registry, free registry cleaner downloads, are widely available online as freeware. Almost all windows operating system from windows 98/2000/20002/xp to the latest windows vista need these registry cleaners for effective and smooth operation. Modifying the system registry can cause serious problems and you might even reinstall the whole operating system. Thus a high performance registry cleaner should be chosen with great care so as not to damage the registry thereby stranding the whole system performance. Most freeware that boast of thorough registry check may not be that useful and as one has to choose these registry cleaners at one's own personal risk, careful study of the free registry cleaner downloads available must be first scrutinized before actually downloading the freeware. Whatever be your ultimate choice the purpose of effective cleaning of the registry is the top priority, which one should never postpone or forget.
Source: http://groups.google.com/group/regrepairsbv/browse_thread/thread/c2259dc0a9f67eae